On May 12th, cyber-security experts worked around the clock to combat an insidious piece of ransomware, dubbed WannaCry, which hijacked thousands of computers in countries across the globe. Now, with sophisticated copycats already being detected, is your business prepared for the next wave of ransomware?
It is no secret that maintaining a high standard of internet security is vital for businesses and individuals alike. Yet, few incidents have reinforced that fact as thoroughly as the recent outbreak of an aggressive piece of malware, dubbed WannaCry.
What is WannaCry? And how do we stop it?
On 12th May 2017, computers around the world were compromised by the malicious software, also known as “WannaCrypt”. On logging in, users were greeted by an onscreen “ransom note”, informing them that their data had been encrypted, and demanding a payment of $300 in Bitcoins for the return of the data to its original state.
Malware that operates in this fashion is typically known as “ransomware”. However, the particular propagation method of WannaCry has caused it to be termed a “ransomworm”. Essentially, it functions as a network worm, automatically spreading to vulnerable systems via an infection vector, publicised by hacker group “The Shadow Brokers” less than a month before this attack.
A fast-moving threat
Using the EternalBlue exploit, WannaCry was able to infect thousands of computers in a matter of hours, bringing organisations around the world to a standstill. In Russia, 1,000 computers belonging to the interior ministry were reported to have been affected. Meanwhile, in the UK, medical staff were left without access to patient records as the ransomworm disrupted 48 separate NHS facilities.
Indonesia, Spain, China, and North Korea were among the affected countries, with the worm attacking computers in schools, hospitals, telecom companies, and local authorities. In the US, FedEx was also confirmed to have been impacted by the attack.
The seemingly haphazard distribution of infection was due to the use of the DoublePulsar and EternalBlue hacking tools, which exploited a vulnerability in the Server Message Block (SMB) protocol implementation in a number of Windows systems.
This vulnerability was a bug in the way the SMB traffic was handled, which meant that a server response, which did not meet the required parameters of the response structure, could enable potentially malicious servers to connect to the Windows system. In the case of WannaCry, this meant the ransomworm could slip undetected into many systems simply by tricking the SMB authentication process.
In March 2017,Windows released the MS17-010 security update. However, this was not available to retired systems, and furthermore, had not yet been installed by everyone with supported systems. Older versions of Windows were particularly vulnerable, as support for these systems ceased several years ago. As such, organisations with outdated or unpatched Windows computers were easy targets for the ransomware.
What you can do right now: Practical steps to stop the spread
Client Versions:
- Windows 10
- Windows 8.1
- Windows 7
- Microsoft Windows Vista SP2
- Windows XP
Server Versions:
- Windows Server 2016
- Windows Server 2012 R2
- Windows Server 2012
- Windows Server 2008 R2 SP1
- Windows Server 2008 SP2
Device Versions:
- Windows RT 8.1
However, all versions of Microsoft Windows are likely to be at risk, so if you own any of these systems, you should update them with the latest security patches immediately. In particular, you should make sure you have installed the MS17-010 patch. In addition to the security updates, you can activate host-based and network firewalls to block TCP/445 traffic from any unknown systems.
Finally, you should also create a regular backup of your data. While you can significantly decrease the chance of malware infecting your systems, there is always a risk that something may slip through the net. However, if the worst should happen, you can still mitigate the damage by having a recent backup of your files.
Finding the killswitch
It was a 22-year-old security researcher who discovered the “killswitch” for the ransomworm. The UK-based researcher, working under the pseudonym MalwareTech, noticed that WannaCry queried an unregistered domain as part of its command string. MalwareTech registered the domain as part of a routine process known as “sinkholing”, which aims to limit malware traffic by directing it to a server designed to capture it.
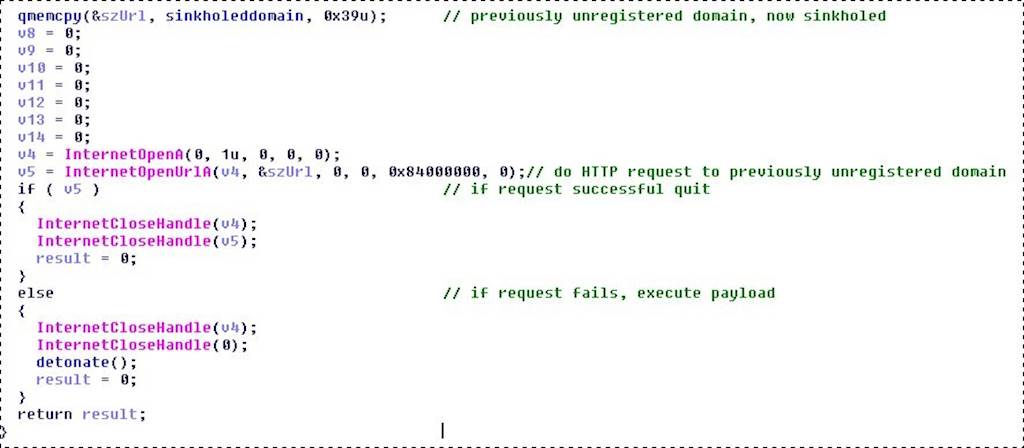
Image credit to: https://www.malwaretech.com
In a stroke of luck, this caused the ransomware to self-terminate, as it had been coded to make an HTTP request to the unregistered domain, then execute its objective when the query failed. If the query was successful, the malware was coded to simply close. As such, once the domain had been registered, the HTTP requests no longer failed, ultimately preventing the ransomware from spreading any further.
While this did not reverse the damage done to those already impacted by the worm, it allowed significant action to be taken to detect and alert people whose computers had been infected. In the meantime, Microsoft released an emergency security patch, including offering support for retired versions of Windows, urging all users to update their computers as soon as possible.
The aftermath: There may be more to come
While the worm spread quickly, it is believed that not many people paid the $300 fee to have their files decrypted. It has been speculated that this may in part be due to the fact the ransomware asked for the payment in Bitcoins.
This cryptocurrency is a popular choice for ransomware operations as it is not only global, but also unregulated by any central bank. All Bitcoins are recorded in a blockchain ledger: an autonomous, distributed database, where data is recorded within time-stamped blocks. These blocks cannot be modified retroactively, making them a secure means of transmitting or storing data.
Unfortunately, despite the rapid success of cybersecurity efforts to shut down the attack, this is likely to be only the beginning. Security services are working to track down those responsible, but the many iterations being released make it hard to pinpoint a source. However, it has been suggested that elements of the code bear resemblance to hacking tools used by the Lazarus Group, known primarily for its attacks on Sony Pictures in 2014.
As MalwareTech states in his blog post on the event, it is possible that future iterations of WannaCry may not contain the weakness that allowed the ransomworm to be shut down. As such it is vital to take steps to secure your devices, even if you have been unaffected by the attack so far.
The exploit used by WannaCry only applies to computers running Windows. However, new forms of malware are constantly being developed, so you should ensure that your security is up-to-date on all computers, and any other devices connected to your network.
How to protect your business from future malware attacks
Falling victim to ransomware, or indeed any form of malware, can be hugely detrimental to your organisation. Not only could you lose valuable data, your business could be brought to a standstill while you work to remedy the issue. Fortunately, there are many things you can do to protect your data, and keep your network secure.
One of the easiest solutions is to upgrade to the latest version of Windows. This ensures you will continue to receive the latest updates and safeguards, protecting your computer from new threats as they emerge. The NHS was allegedly given multiple warnings that using outdated systems would leave them vulnerable to attack.
In addition, you should have a system in place for regularly backing up files and sensitive data. This means your data can remain safe, even if your computer becomes infected. This could be an offsite server, or even a physical backup that is not connected to your network.
Firewalls and anti-virus options
A computer’s firewall serves as its first line of defense against malware, detecting connections from unknown sources, and blocking suspicious traffic. Coupled with an effective antivirus and antimalware suite, this can greatly improve the safety of your network. There are several types of protection available, each of which has a slightly different function.
Choosing a Firewall [Checklist]
How do you know if you're choosing the right firewall?
GET ACCESS ifp.ClickDetails"The most common antivirus product is a disk scanner, which runs through the contents of all files, disks, and directories, identifying potential threats, and quarantining them. Similarly, you could benefit from running a start-up scanner, which performs a quick check of your system files and boot sectors when you turn on your computer. The purpose of this is to catch and terminate boot sector viruses, before they are able to take effect.
Another approach to virus protection is to install software which runs quietly in the background. These products use behaviour-based detection, which monitors for “virus-like activity” and intercepts it. This can be used in conjunction with a memory-resident scanner, which is configured to perform targeted scans based on particular triggers, such as running a program or executing a file.
Keep your system up to date
Once your security system is up to date, you can fine-tune it by testing for weaknesses. Software development platforms, such as the Metasploit Framework, allow you to develop exploit modules and similar tools for testing the limits of your system. By identifying vulnerabilities, you can continuously make improvements, and maintain a high standard of security throughout your organisation.
Of course, no amount of security can account for human error, so the final, crucial step in securing your network is to ensure all employees have a good understanding of cyber security, and appropriate use of work computers. In particular, remind everyone to beware of links in emails and other messages, even if the sender appears to be someone they know.
It can seem like a lot to take in, but once you make these initial changes, it is a simple thing to stay up-to-date, and informed. It is never worth compromising on internet security, as it puts not only your data and devices at risk, but also the trust of your clients, and the reputation of your business. However, a comprehensive security strategy can put your mind at ease, while constantly preparing you for the ever-changing future of malware.
Access the latest business knowledge in IT
Get Access



Comments
Join the conversation...