This article was updated 16th December 2020.
Adaptive security remains one of the biggest trends in IT and the industry is expected to grow at a CAGR of over 15% in the next five years.
What is Adaptive Security Architecture?
Because digital businesses are reliant on a complex matrix of infrastructure, software and processes – as well as human resources - traditional ‘prevent and detect’ approaches to security are being superseded by more agile models that apply a continuous and coordinated methodology.
As far back as 2008, Sun Microsystems produced a paper, Designing an Adaptive Security Architecture, outlining a blueprint for creating an adaptive security model. Adaptive security architecture describes an approach that uses a combination of integrated tactics to help businesses stay ahead of cybercriminals, instigating flexible security measures to protect data and systems in as agile a way as possible, rather than relying on outdated perimeter defense strategies.
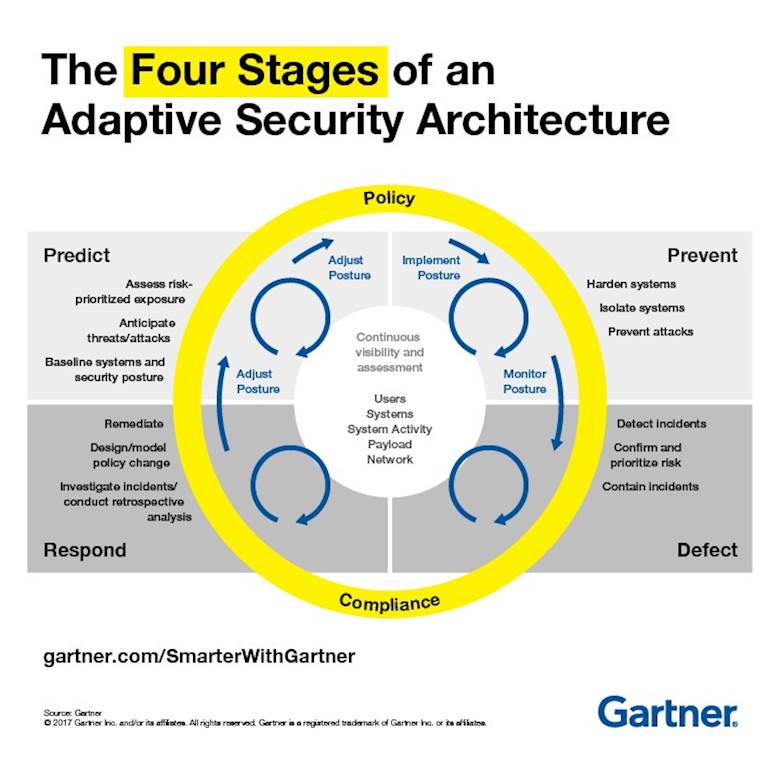
Four stages of adaptive security architecture
Traditional prevention and detection methodologies, like deploying antivirus software, IDS/IPS and firewalls, have become less effective as organizations integrate a range of resources – such as cloud-based systems and open-source APIs – into their business ecosystem. Tech is no longer restricted to closed, in-house teams, instead inviting collaboration and exploring new paths.
Gartner believes that every organization needs to start with the assumption that security will be breached at some point, making continuous monitoring the only viable approach – a system that cycles through a constantly repeated loop that aims to predict, protect, detect and respond to threats.
Advancements through AI
Gartner predicts that machine learning and artificial intelligence (AI) will also feed into adaptive security architecture. This approach is effectively illustrated by a system called ‘user and entity behavior analytics’ (UEBA) which profiles users and network devices to gain an understanding of what constitutes normal behavior, so it can highlight anomalies when they occur.
Importantly, for Gartner, the key to the effectiveness of this and other approaches is its seamless integration in an organization’s architecture, which is only possible with cross-departmental cooperation and collaboration.
New tools to tackle an uncertain future
Many businesses don’t feel equipped to handle the escalated attack threat that has become part of the digital landscape – some even stockpile bitcoins to pay ransoms when their systems succumb to the inevitable hack. But by integrating widespread and continuous risk-based response protocols that include ‘improved prevention, detection, response and prediction capabilities’, Gartner suggests that it is possible to protect against advanced threats.
- Processes designed to prevent attacks will block known threats before they create damage
- Sound detection tools will reduce the impact of threats as they limit the time they have to act on a system
- A quick response to investigate any security issues that are discovered will help avoid a recurrence of the same threat
- Predictive technology will use community-sourced information to anticipate potential threats
An adaptive approach to security can save time and resources and empower teams to engage in prompt action that will limit serious data loss or systems damage.
Access the latest business knowledge in IT
Get Access





Comments
Join the conversation...